North Korea cryptocurrency theft: How state-backed hacks are reshaping crypto security
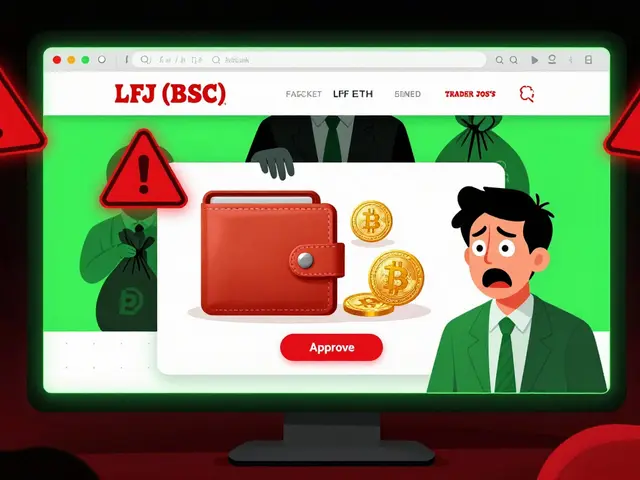
When you hear about North Korea cryptocurrency theft, state-sponsored cyber operations targeting digital assets to fund national programs, you’re not hearing about random hackers. You’re hearing about one of the most organized, well-funded, and persistent criminal entities in crypto: the Lazarus Group, a North Korean hacking collective linked to the country’s military intelligence. This isn’t petty theft—it’s a systematic campaign that’s stolen over $3 billion since 2017, according to blockchain analysts at Chainalysis and the UN. Their targets? Exchanges, bridges, DeFi protocols, and even individual wallets with weak security. And they’re not slowing down.
Their method is simple: find the weakest link. Most attacks happen through cross-chain bridges, third-party systems that move crypto between blockchains. These bridges are often poorly audited, have centralized control points, and lack real-time monitoring. Lazarus Group exploits this. They’ve hacked ThorChain, Ronin, Harmony, and more—each time walking away with millions in ETH, BTC, and stablecoins. They don’t need to break into wallets. They trick the system into sending them the money. And once the funds are moved, they’re laundered through mixers, converted into privacy coins like Monero, or cashed out via P2P platforms in countries with weak oversight.
What makes this different from regular crypto scams? It’s scale, persistence, and backing. While most scammers need to lure one person into a fake airdrop, Lazarus Group runs full-scale cyberwarfare operations with government resources. They hire elite coders, use zero-day exploits, and have teams dedicated to social engineering and fake identities. Their goal isn’t just money—it’s funding a regime under sanctions. That’s why governments like the U.S. and South Korea have started treating these attacks like acts of war. The North Korea cryptocurrency theft problem isn’t going away. It’s getting smarter. And the only defense? Better security practices, avoiding untrusted bridges, using hardware wallets, and never giving up private keys—even to "official" support teams. Below, you’ll find real cases, breakdowns of how these hacks worked, and what you can do to avoid becoming the next victim.
How North Korea Funds WMD Programs with Stolen Cryptocurrency
North Korea has stolen over $3 billion in cryptocurrency since 2017 to fund its nuclear and missile programs. State-sponsored hackers use social engineering, crypto mixers, and global networks to evade sanctions and bypass traditional financial controls.